PopsiclePete
Mission programmer
Since we have committed ourselves to giving more frequent updates on our progress, I thought I would offer a glimpse at one of the lesser known aspects of Standoff's development: patch making!
As you know, Standoff is a modification of Secret Ops. Even if SO is much easier to mod than the previous WC games, many aspects of the game were hardcoded into it: the number of guns, number of ships, number of displayed asteroids, etc. To be able to break those limitations, the main game's EXE has to be altered. Those of you who have tried hex-editing their favorite games knows you can't do much using that method. To solve this problem, WC editing guru HCl developed a very effective method: do a very small hack to the EXE so it loads a DLL, and from that DLL rewrite the EXE directly in memory!
Using this trick, HCl has made many amazing patches to WCP/SO, like the hi-res and DVD patches. He also made a number of patches for Unknown Enemy and Standoff... but the really cool thing is that he gave us a formidable tool through which we've been able to add on our own little patches every time a need arises.
At this stage in the Episode 5 development, Standoff includes over 80 patches which allow us to raise the limits of the original SO, add new mission commands and making the game closer to the original Wing Commander 2 gaming experience.
I have prepared a small demonstration explaining a very simple patch I recently made. After hearing people complain about the game's screenshots being overwritten with new images every time the game was reloaded, I decided to make a quick patch. The problem is that when the player hits the "Print Screen" key, the game doesn't check for existing files and starts to save them over what already exists.
Here is a simplified description of how the patching process works.
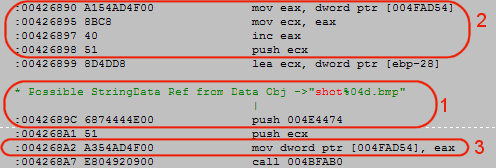
Doing a quick search in the game's EXE to find where the screenshot's name is chosen is easy (see image, tag 1). If you look at the lines just over the reference to the filename (tag 2), you can see that the EXE retrieves some value, make a copy of it (eax to ecx) then increments the value. This value is then stored back (tag 3). This obviously is the counter.
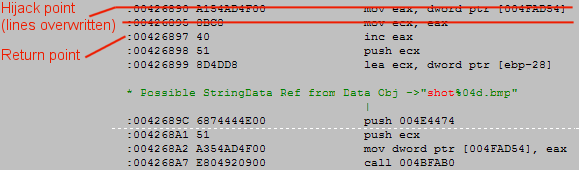
What we'll do is hijack the original code: we'll rewrite the game to load a custom function we made in the DLL. A first function, run immediately after the EXE is loaded into memory, will overwrite two part of the original code to make it call our custom function instead.
So, now we have the game calling a funtion named "ScreenshotCounter_hook". Now what ? "ScreenshotCounter_hook" will contain assembler code to continue the sequence where we hijacked the EXE. But since I suck at assembler code and I want to code lazily in C++... so while we could have the hooking function do whatever patching we need, we often have it call a nice C++ function. That's what we'll do here. Note that we usually want to restore a few lines of the code we've overwritten; I've done it here even if it wasn't necessary (those with a sharp eye will understand, looking at the code, that our patch will completely disregard the internal screenshot counter, so it's not important to actually read it's value!):
Then comes the C++ code to check is a screenshot file already exists before passing a screenshot number back to the game:
And voilà! I hope you enjoyed this little peek into the Standoff patching process. Many, many thanks to HCl who developed the technique and made the essential patches that now allow us to go further and make a great mod! Now, I will go back to actually making the game instead of writing stuff...
Oh, and if you want to learn more about DLL patching, HCl has made much more information available on his techniques on his website. Everything is there, from the initial alteration that has to be done to the EXE to complete source of the DLLs for UE and Standoff Episode 1.
Pierre
As you know, Standoff is a modification of Secret Ops. Even if SO is much easier to mod than the previous WC games, many aspects of the game were hardcoded into it: the number of guns, number of ships, number of displayed asteroids, etc. To be able to break those limitations, the main game's EXE has to be altered. Those of you who have tried hex-editing their favorite games knows you can't do much using that method. To solve this problem, WC editing guru HCl developed a very effective method: do a very small hack to the EXE so it loads a DLL, and from that DLL rewrite the EXE directly in memory!
Using this trick, HCl has made many amazing patches to WCP/SO, like the hi-res and DVD patches. He also made a number of patches for Unknown Enemy and Standoff... but the really cool thing is that he gave us a formidable tool through which we've been able to add on our own little patches every time a need arises.
At this stage in the Episode 5 development, Standoff includes over 80 patches which allow us to raise the limits of the original SO, add new mission commands and making the game closer to the original Wing Commander 2 gaming experience.
I have prepared a small demonstration explaining a very simple patch I recently made. After hearing people complain about the game's screenshots being overwritten with new images every time the game was reloaded, I decided to make a quick patch. The problem is that when the player hits the "Print Screen" key, the game doesn't check for existing files and starts to save them over what already exists.
Here is a simplified description of how the patching process works.
Doing a quick search in the game's EXE to find where the screenshot's name is chosen is easy (see image, tag 1). If you look at the lines just over the reference to the filename (tag 2), you can see that the EXE retrieves some value, make a copy of it (eax to ecx) then increments the value. This value is then stored back (tag 3). This obviously is the counter.

What we'll do is hijack the original code: we'll rewrite the game to load a custom function we made in the DLL. A first function, run immediately after the EXE is loaded into memory, will overwrite two part of the original code to make it call our custom function instead.
Code:
{
void * t = (void *) ScreenshotCounter_hook;
char bridge[] = {0x68, 0,0,0,0, 0xc3};
memcpy (bridge+1, &t, 4);
memcpy((void*)0x426890, bridge, 6);
}
So, now we have the game calling a funtion named "ScreenshotCounter_hook". Now what ? "ScreenshotCounter_hook" will contain assembler code to continue the sequence where we hijacked the EXE. But since I suck at assembler code and I want to code lazily in C++... so while we could have the hooking function do whatever patching we need, we often have it call a nice C++ function. That's what we'll do here. Note that we usually want to restore a few lines of the code we've overwritten; I've done it here even if it wasn't necessary (those with a sharp eye will understand, looking at the code, that our patch will completely disregard the internal screenshot counter, so it's not important to actually read it's value!):
Code:
void __declspec(naked)ScreenshotCounter_hook(void) {
__asm {
mov eax, dword ptr[0x4FAD54] // restore the overwritten code
call CheckScreenshotNumberExists
mov ecx, eax // restore the overwritten code
push 0x426897 // return code location
ret
}
}Then comes the C++ code to check is a screenshot file already exists before passing a screenshot number back to the game:
Code:
int screenshotNumber = 0; // new counter
int __stdcall CheckScreenshotNumberExists() {
char filenameCheck[32];
sprintf(filenameCheck, "shot%04d.bmp", screenshotNumber);
while(FileExists(filenameCheck)) // as long as the file exists...
{
screenshotNumber++; // ... increment the counter
sprintf(filenameCheck, "shot%04d.bmp", screenshotNumber); // ...recheck
}
return screenshotNumber; // return the new counter value
}And voilà! I hope you enjoyed this little peek into the Standoff patching process. Many, many thanks to HCl who developed the technique and made the essential patches that now allow us to go further and make a great mod! Now, I will go back to actually making the game instead of writing stuff...
Oh, and if you want to learn more about DLL patching, HCl has made much more information available on his techniques on his website. Everything is there, from the initial alteration that has to be done to the EXE to complete source of the DLLs for UE and Standoff Episode 1.
Pierre